
Research indicates that 95% of breaches are financially motivated, with 83% involving external actors. In a digital landscape where cybercrime threatens to surpass the combined market capitalization of industry giants like Apple, Microsoft, and Google, safeguarding your business from potential threats is no longer a luxury but a necessity.
This underscores the pivotal role of Cyber Threat Intelligence in converting potential risks into strategic advantages. Let’s delve deeper.
What is Threat Intelligence?
As the term implies, threat intelligence refers to data-driven insights into potential cybersecurity threats that businesses can leverage to proactively identify and mitigate risks. It offers invaluable information about the tactics, techniques, and procedures employed by adversaries, bolstering your defense mechanisms and incident response strategies with targeted security measures.
Why is Threat Intelligence Essential?
In today’s era of sophisticated cyber-attacks, threat intelligence is indispensable for outmaneuvering equally sophisticated cybercriminals. As outlined in the Pulse of Creativity Annual Threat Intelligence Report 2023, the threat landscape is multifaceted, evolving from ransomware assaults to QR code phishing (“quishing”).
While certain industries like manufacturing and healthcare face escalating targeted attacks, others such as finance, education, government, and energy are not immune to their repercussions. A Threat Intelligence Platform translates these insights into actionable strategies, transitioning businesses from reactive to proactive defense postures.
Cyber Threat Landscape: Review and Future Prospects
According to a recent survey by CyberRisk Alliance (CRA), over 39% of respondents are already leveraging threat intelligence to thwart or mitigate cyberattacks. An even more noteworthy statistic: 55% are preparing to integrate Cyber Threat Intelligence (CTI) into their security frameworks.
The question arises: why are numerous organizations prioritizing threat awareness, and how might it impact them? Let’s recap some notable headlines from the past year:
- A dating app boasting 50 million users falls victim to data breaches. (ET CISO)
- Attackers inundate the NPM Repository with over 15,000 spam packages containing phishing links. (The Hacker News)
- Cybercriminals utilize ChatGPT to streamline their operations, as reported by Business Insider.
- The Russian hacktivist group KillNet targets U.S. hospitals with DDoS attacks. (BlackBerry)
- Google exposes a 0-click bug in the Pixel 6 modem and advises users to disable 2G. (Malware.News)
- Rutgers, Stony Brook, and other universities warn of data exposure resulting from the MOVEit Hack. (Bloomberg)
These insights merely scratch the surface. Gartner predicts that nearly half of cybersecurity leaders will switch jobs by 2025 due to burnout and stress stemming from potential breaches. Concurrently, a shortage of talent may exacerbate incident rates, underscoring a concerning cycle of stress and scarcity in the field.
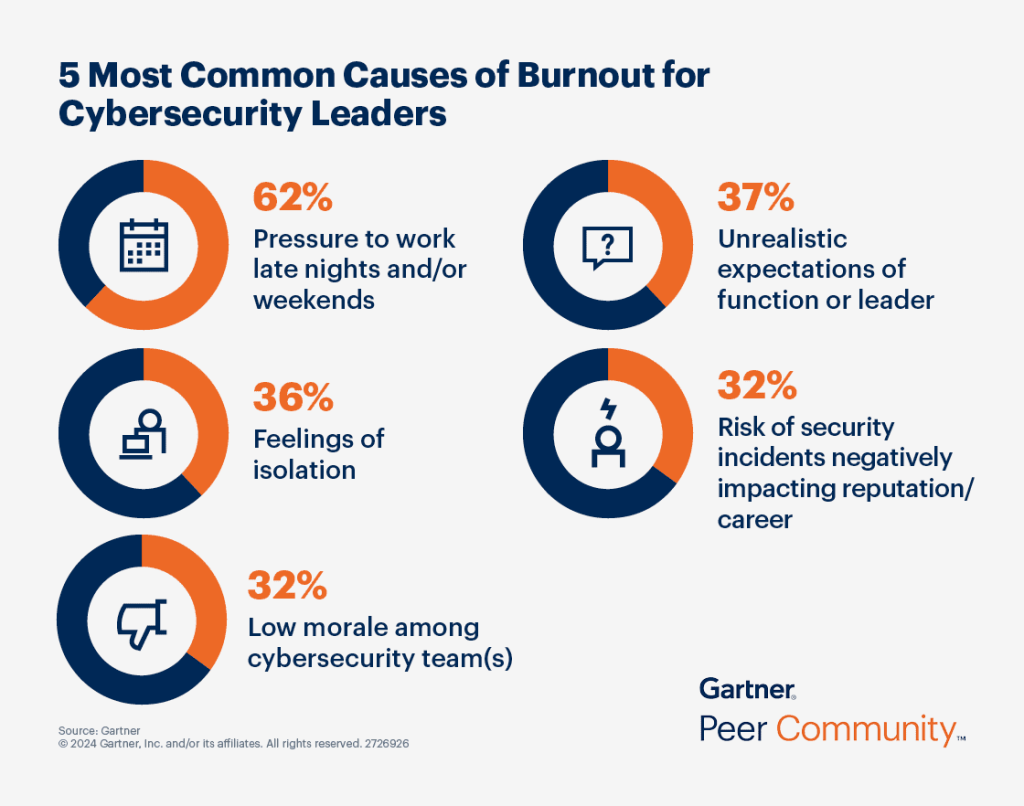
These highlighted challenges underscore the critical importance of implementing a tailored threat intelligence strategy that comprehensively understands the nature and potential of current threats, while intelligently preparing businesses to prevent and respond to identified vulnerabilities with strategic measures.
How do Threat Intelligence Platforms (TIP) protect your business?
Organizations often overlook external cyber threats while engrossed in analyzing internal logs or incident reports. An external threat intelligence platform bridges this gap with its extensive tools and modules, assisting businesses with a strategic cybersecurity incident response and remediation approach — fundamentally altering how businesses perceive, identify, and respond to sophisticated incidents.
Industry-specific threat visibility: Provides businesses with unparalleled insight into threats specifically targeting their industry. This capability ensures organizations are constantly informed about the activities and tactics of cybercriminals and hacktivists, empowering them to tailor their defenses to the unique challenges they face.
Proactive defense transformation: Enables organizations to shift from reactive to proactive by offering insights into global threats aimed directly at the business’s defense state. With a forward-looking approach, TIP allows for preemptive identification and mitigation of potential threats, ensuring a more secure operational environment.
Customized intelligence and remediation guidance: Offers tailored intelligence research, including remediation guidance and solutions specific to an organization’s needs. This personalized approach significantly enhances the security posture of the business by providing actionable insights and strategies designed to address unique vulnerabilities.
Comprehensive threat analysis: Contextualized threat intelligence platforms analyze suspicious files and behaviors to uncover the entire scope of an attack, from inception to execution. This comprehensive analysis aids in making informed security decisions, leveraging advanced research and cloud technology scalability to offer superior protection.
Streamlined security investigations: Integrating threat intelligence into security operations streamlines the investigation process by delivering timely and relevant information, significantly reducing the time required for security analysts to make informed decisions and optimizing the response to suspicious behaviors.
Flexible integration and accessibility: Easily integrates into existing IT infrastructures and applications, offering valuable insights through API requests. Available through various marketplaces, these platforms seamlessly enhance an organization’s threat intelligence capabilities, driving forward security innovation.
Standardization and collaboration: Improves intelligence sharing and operational consistency by adopting standardized reporting formats and common language frameworks, such as the MITRE ATT&CK matrix. By facilitating engagement in information-sharing centers and interoperability between contextualized threat intelligence tools, these platforms amplify a collaborative approach to defense and bolster collective cybersecurity resilience.
How Pulse of Creativity transforms Threat Intelligence into a strategic business asset?
Comprehensive visibility with threat data feeds: By enabling continuous access to enriched and contextualized Indicators of Compromise (IOCs), Pulse of Creativity empowers your business with real-time, actionable cyber threat intelligence into your security infrastructure. This not only enhances forensic capabilities but also equips you with insights needed to preemptively neutralize potential threats, ensuring uninterrupted and secure operations.
Proactive defense with threat advisories: Pulse of Creativity’s timely threat advisories transform information into action by providing early warnings about emerging threats. This proactive approach shifts your organization from reactive to proactive defense posture, mitigating risks before they escalate into costly breaches and leveraging a resilient cybersecurity posture.
Strategic clarity with APT Intelligence Reporting: Gain a thorough understanding of Advanced Persistent Threats (APT) tactics, techniques, and procedures with exclusive APT intelligence reporting from Pulse of Creativity. Insights into APT actors’ nuances help your organization implement targeted defenses, minimizing sophisticated attack risks and safeguarding critical assets with strategic clarity.
Financial threat intelligence for asset protection: Pulse of Creativity anticipates and thwarts financially motivated cyber threats with comprehensive analysis of malware campaigns and early warning systems. Stay informed about the latest financial cybercrime tactics to protect financial assets and ensure transaction integrity, preserving customer trust and your organization’s reputation.
Transforming Threat Intelligence into business strength
In a world where threats are inevitable, Pulse of Creativity ensures readiness and resilience. Our Threat Intelligence Platform is not just a tool but a strategic ally in the fight against cyber threats. With extensive modules covering contextualized threat intelligence feeds, stolen credentials, dark web monitoring, social media, digital footprint monitoring, and beyond, we provide a holistic approach to cybersecurity.
By transforming threat intelligence into actionable insights and proactive defenses, we help you not only mitigate risks but also transform them into opportunities by seamlessly integrating with 170+ tools and offering 750+ automated actions.
Whether you’re a third-party vendor or a security team seeking external threat intelligence to supplement or refine existing security solutions and infrastructure, explore our specialized assessments and transformative consultancy to find the right fit for your defense use case. Get in touch with our experts today.