
Did you know that the US has consistently borne the highest data breach costs, hitting USD 9.48 million, showing a slight increase from USD 9.44 million, for thirteen consecutive years?
Following closely are the Middle East (USD 8.07 million), Canada (USD 5.13 million), Germany (USD 4.67 million), Japan (USD 4.52 million), and the UK (USD 4.21 million) (Statista, 2024).
The global surge in cyberattacks is no coincidence. It’s a direct result of the rapidly evolving technology landscape. From the impact of COVID-19 and the rise of remote work to advancements like Generative AI, the headlines are filled with technological shifts. Malicious tools such as FraudGPT, WormGPT, ChaosGPT, DarkBERT, and DarkBART, along with emerging threats like QR code phishing and denial-of-service (DDoS) attacks, highlight the urgent need for robust incident response planning.
This blog aims to provide a comprehensive understanding of incident response (IR) and how proactive defense strategies can safeguard businesses and users against unforeseen digital threats.
What is Incident Response (IR)?
Incident Response, also known as cybersecurity incident response, involves a combination of processes and technologies to detect and respond to cyber threats, attacks, or breaches. It’s a systematic approach within the incident management lifecycle aimed at proactively preventing cyberattacks and minimizing damage without disrupting business operations. By streamlining alert monitoring and reducing response times, security operations teams can focus on strategic threat hunting.
What is an Incident Response Plan (IRP)?
Think of an Incident Response Plan as a strategic playbook for addressing digital security emergencies. It’s a set of guidelines outlining what an organization should do in the event of a security incident to minimize impact.
How does an organization develop one?
Developing an Incident Response Plan involves implementing a risk-based approach, incorporating formal processes and technologies to promptly detect and contain threats. Tailored to each organization’s unique environment and specific threats, this plan is regularly updated for ongoing relevance and effectiveness. It details actionable security incidents, assigns roles, defines task timelines, and provides clear instructions.
Why prioritize an Incident Response Plan?
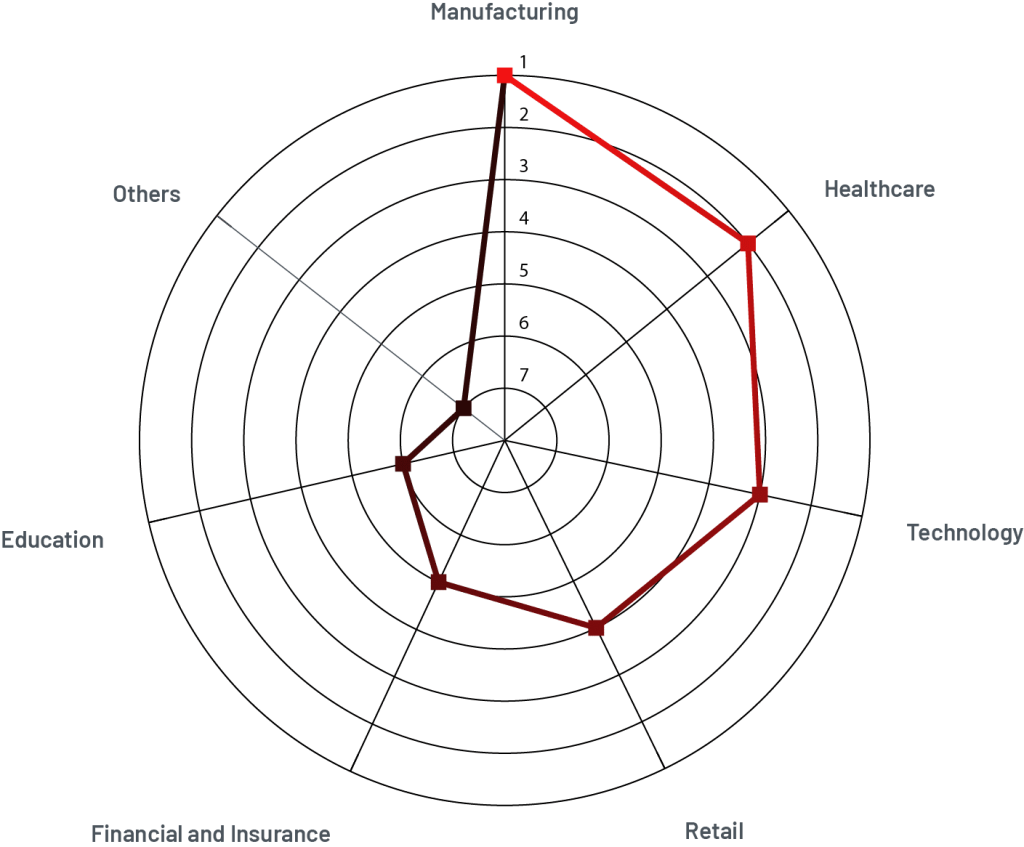
Prioritizing an Incident Response Plan is essential due to the indiscriminate nature of cyberattacks, which target individuals, businesses, and industries indiscriminately. Our Threat Intelligence Report – 2023 indicates that while the manufacturing industry remains a prime target, the past year witnessed intensified attacks on healthcare, technology, and retail sectors. For instance, the healthcare industry faced data breach costs of approximately USD 10.93 million. Additionally, the financial and insurance sectors encountered significant cyber threats, including ransomware attacks and Advanced Persistent Threat (APT) groups. As a result, this year, education, government, public services, and energy sectors are at heightened risk of cyberattacks.
Incident Response Plan (IRP) Frameworks
Two prominent IR frameworks, the National Institute of Standards and Technology (NIST) and SysAdmin Audit Network Security (SANS), are widely utilized by organizations to equip their IT teams in establishing robust incident response planning.
NIST Framework:
The NIST Framework offers an integrated approach, combining containment, eradication, and recovery, ideal for rapid response to significant, complex incidents. It’s favored for its holistic, less compartmentalized handling of incident response.
SANS Framework:
The SANS Framework provides a structured, phase-by-phase process with clear roles and responsibilities suitable for methodical, step-by-step incident management. It’s ideal for environments requiring detailed phase tracking and documentation.
It’s crucial to note that there’s no singular “right” or “wrong” approach. Framework selection often depends on organizational needs and situations. Both frameworks are highly respected and widely used in cybersecurity, each with unique strengths and applications.
Now, let’s delve into the six steps outlined by the SANS framework:
Phase 1: Preparation
Goal: Establish a foundation for incident management readiness
Comprehensive preparation is essential before any incident. Organizations conduct rigorous risk assessments, adapt security policies for emerging threats, and provide training for all personnel to recognize and respond to cyber threats. Templated incident response plans clarify roles across the organization, and lessons learned from incidents are documented to enhance future incident management strategies.
Phase 2: Identification
Goal: Detect incidents and collect indicators of a breach
Security teams sift through daily alerts to distinguish real threats from false positives. Internal and external detection systems are combined for a comprehensive approach. Upon identifying an incident, a thorough investigation ensues, documenting crucial details such as the breach’s source and type.
Phase 3: Containment
Goal: Rapidly isolate threats
Swift action is taken to minimize potential damage. The immediate priority is to isolate affected applications or systems, cutting off attackers’ access and preventing further penetration into the network.
Phase 4: Eradication
Goal: Thoroughly eliminate threats
Following containment, efforts focus on completely removing any trace of attackers and malware from the system. Systems are cleaned, restored from clean backups, or reimaged as needed, adhering to company policies throughout.
Phase 5: Recovery and Reflection
Goal: Restore normal operations and evaluate incident response effectiveness
Normalcy is restored, and incident response steps are evaluated for effectiveness. Plans and processes are updated, and ongoing training ensures continuous improvement and readiness for future incidents.
Phase 6: Lessons Learned
Goal: Document incidents and enhance future incident response strategies
A comprehensive review is conducted to learn from the incident, fortifying the organization’s overall preparedness for future incidents.
Did you know? A Ponemon survey revealed that 77% of participants lack a consistently applied formal incident response plan within their organizations. These findings underscore the vital need for a robust incident response plan, especially given the increasing severity of cyberattacks.
How can Pulse of Creativity Incident Response Services assist you?
Whether managing internally or outsourcing some or all incident response activities, Pulse of Creativity Incident Response Services can streamline the pathway to security. With recognized expertise and cutting-edge tools, our team empowers organizations against evolving cyber threats, ensuring Confidentiality, Integrity, and Availability (CIA). Connect with our experts to tailor your Incident Response Playbook and enhance your incident response capabilities!